1. Enhancing Wireless Network Coexistence via Interference Cancellation
In the increasingly crowded spectrum sharing mechanisms are desired to enable coexistence among disparate multi-hop wireless networks. Cross-technology interference (CTI) is widespread, detrimental to network performance (e.g., between LTE and WiFi networks). Current approaches focus on interference avoidance, separating transmissions in frequency, time, or space, rather than reducing or eliminating interference. Advancements in physical layer technologies like Multiple Input Multiple Output (MIMO) interference cancellation (IC) enable interference-free concurrent transmissions. This project seeks to develop new models and methodologies to theoretically quantify the performance limit of cross-technology IC, as well as designing practical protocols to enable interference-free coexistence.
Funding support: National Science Foundation, CAREER: Toward Cooperative Interference Mitigation for Heterogeneous Multi-hop MIMO Wireless Networks, 7/1/2014-6/31/2019, PI (Project website).2. Enhancing Wireless Network Performance with Reconfigurable Antennas
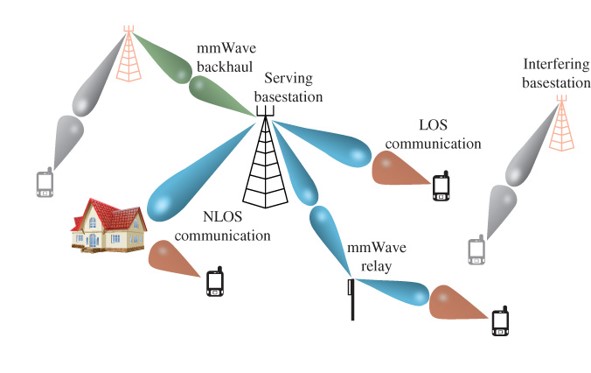
As the number of wireless devices and their data demands surge, multi-hop wireless networks (MWNs) require higher capacity, reliability, and quality-of-service (QoS). Traditional approaches, focusing on network-layer mechanisms, struggle to address the fundamental challenge of unreliable wireless channels. Our research systematically explores antenna-level reconfigurability to optimize end-to-end performance and QoS in MWNs. We lay the theoretical foundations and develop practical protocols. Additionally, we leverage online machine learning algorithms to adapt to dynamic link conditions and optimize end-to-end scheduling and routing. This research has impact on networks operating in both sub-6GHz and mmWave bands.
Funding support: Office of Naval Research (ONR), "Toward High Performance Tactical Multi Hop Wireless Networks via Exploiting Antenna Reconfigurability", 6/1/2016-5/31/2019, PI.3. Wireless Security: Automatic Trust Establishment for IoT
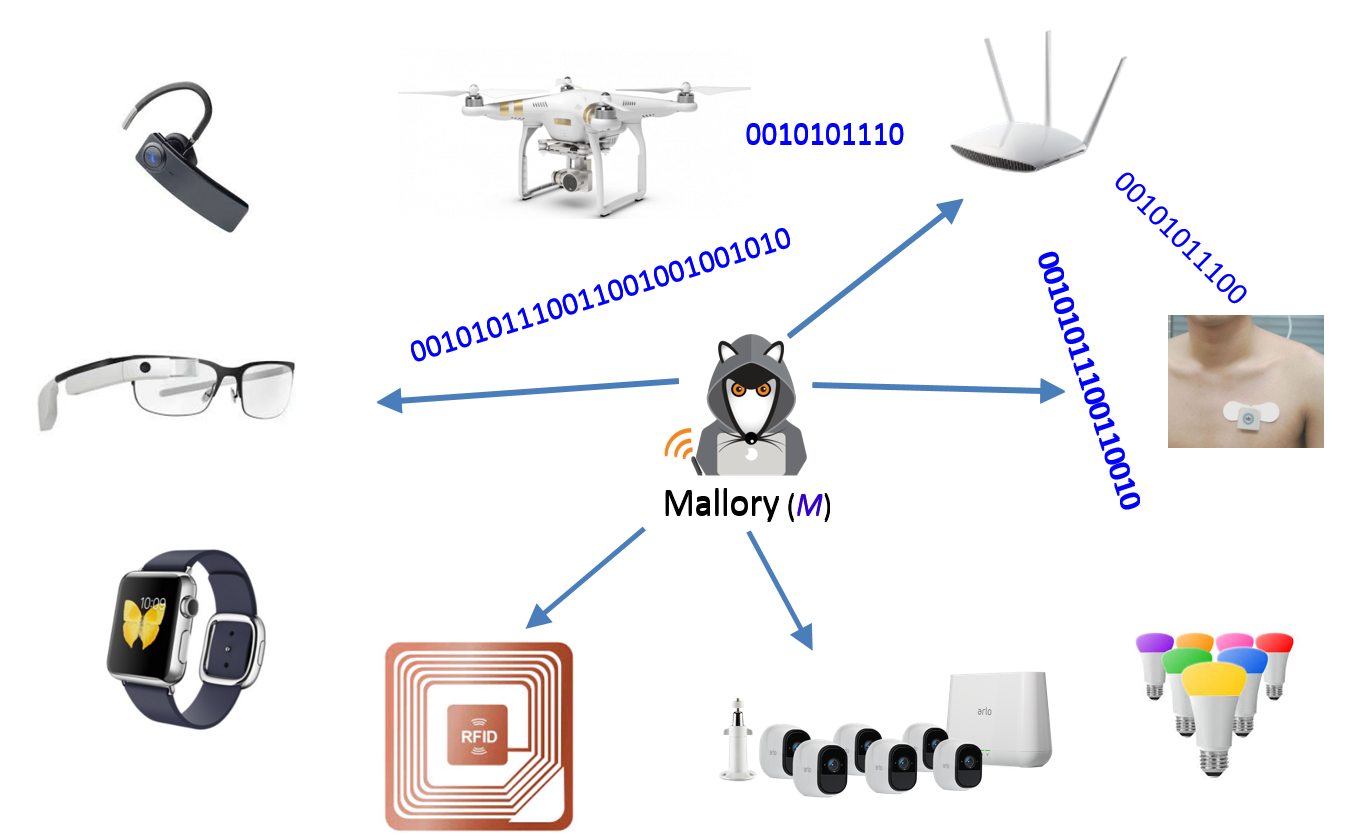
Wireless networks are critical for collecting data from IoT sensors, such as wearable health monitors and security cameras. Ensuring the security, integrity, and availability of these communications is paramount for user safety and privacy. Establishing initial trust, involving mutual authentication and key agreement, is a fundamental step. Traditional methods, like manual key input or pre-loaded secrets, face scalability, usability, and security challenges. PKI-based solutions struggle with key revocation, especially in intermittently connected environments. Our research develops in-band solutions to automate initial trust establishment and trust evolution. This approach requires only a common radio interface, eliminating the need for out-of-band channels or additional hardware. By addressing these challenges, we aim to enhance the security and reliability of wireless IoT networks.
Funding support:4. Security and Privacy of Dynamic Spectrum Access
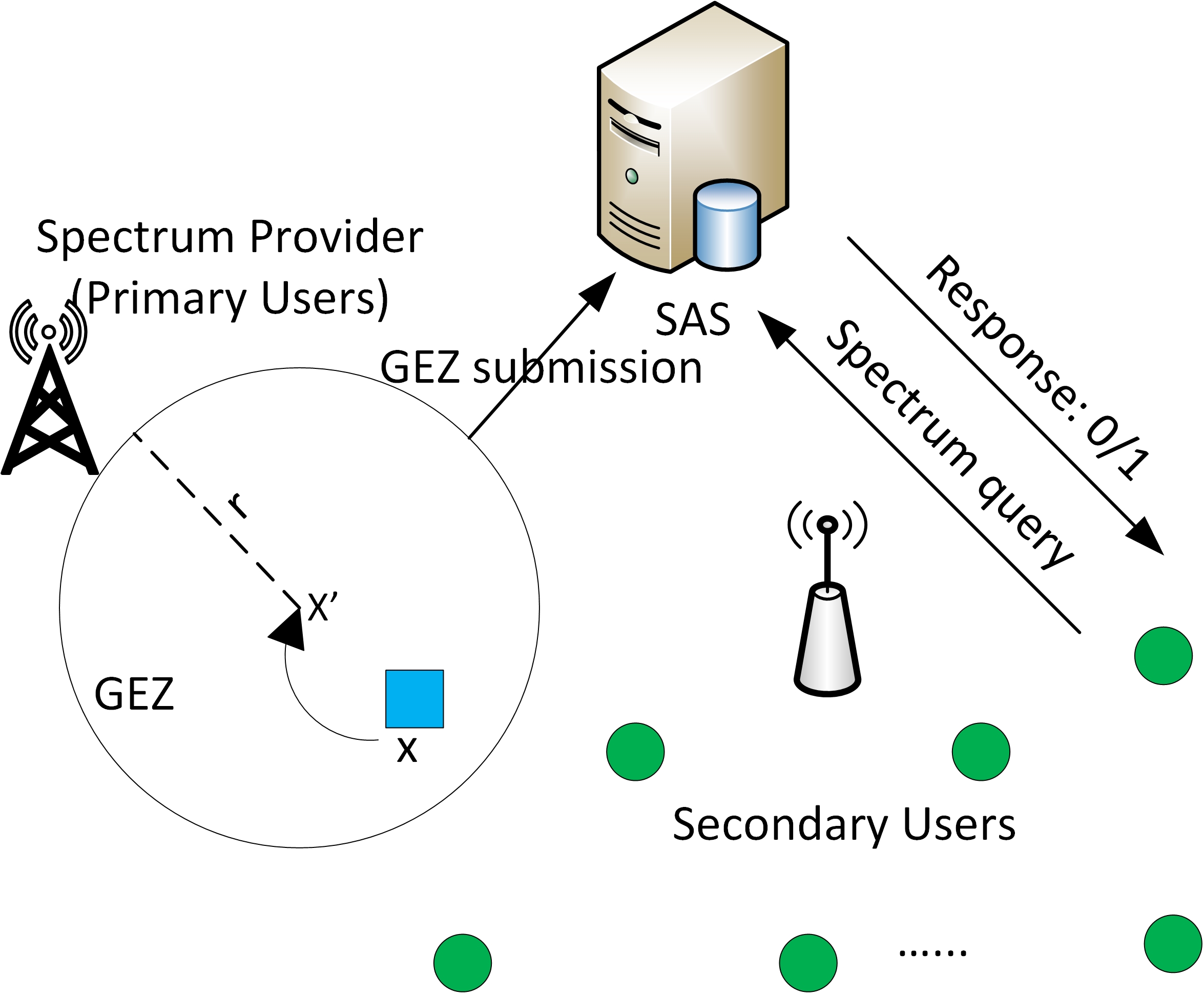
The growing demand for wireless services has led to spectrum scarcity and the need for coexistence of diverse wireless technologies. This coexistence poses significant challenges due to heterogeneity, scale, and lack of coordination. Traditional approaches to spectrum access enforcement, relying on trusted hardware or dedicated devices, are costly and incompatible with legacy devices. To address these issues, we propose a novel framework for secure, efficient, and privacy-preserving spectrum access coordination. We also explore a crowdsourcing-based approach for spectrum etiquette enforcement, leveraging the collective power of cognitive radio devices to detect and deter spectrum misuse without relying on centralized infrastructure.
Funding support:
5. Secure and Privacy-Preserving Data Sharing and Analytics
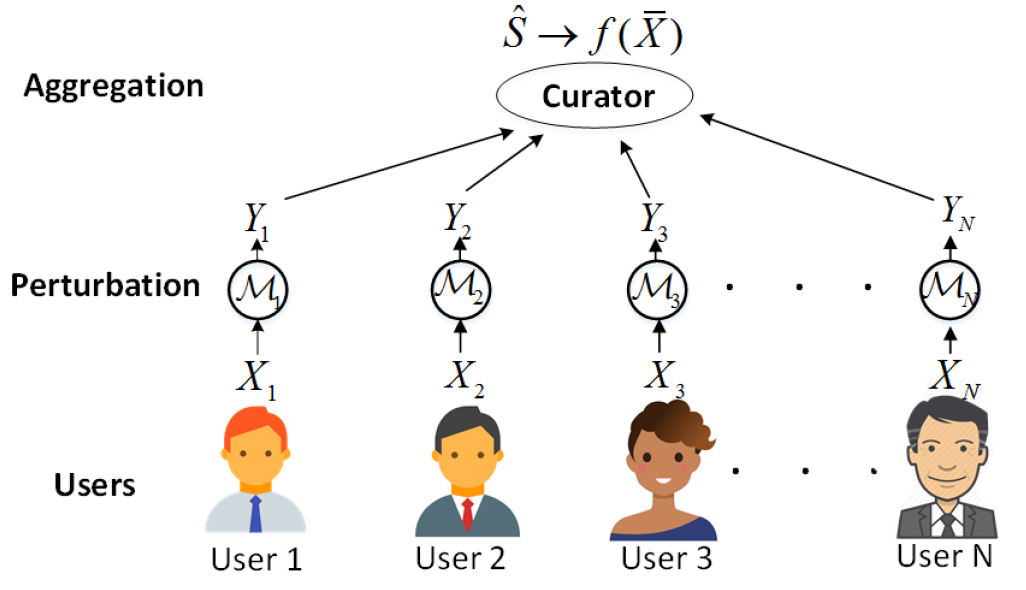
Cloud computing offers scalable and cost-effective data storage and processing, but raises significant security and privacy concerns. Our research aims to address these challenges by developing privacy-preserving solutions for sensitive data stored in public clouds. We focus on: 1) Data Possession Proofs: Ensuring data owners retain control over their data in the cloud. 2) Privacy-Preserving Search: Enabling secure and private data search within cloud environments. 3) Collaborative Cloud Computing: Facilitating secure and private collaborative computations on cloud data. Additionally, we explore novel data purturbation techniques to balance privacy and utility in scenarios where data is collected for analytics and personalized services. We investigate context-aware privacy notions and mechanisms to enhance the utility-privacy trade-off, leveraging statistical and information-theoretic approaches.
Funding support:6. Secure and Resilient Vehicle Platooning

Vehicular platooning promises to revolutionize transportation. While it offers opportunities for increased efficiency and safety, it also introduces new security risks. Our research aims to secure automated vehicles by: 1) Identifying vulnerabilities: We examine vulnerabilities in inter- and intra-vehicle communication and control systems. 2) Developing defenses: We propose practical, low-overhead defense mechanisms, including physical layer security techniques. 3) Supporting phased deployment: We consider a three-phase deployment: local autonomy, vehicle-to-vehicle communication, and vehicle-to-infrastructure communication. By addressing these challenges, we aim to ensure a safe and secure future for automated transportation.
Funding support: National Science Foundation, TWC: Medium: Secure and Resilient Vehicular Platooning, 8/1/2014-7/31/2019, Co-PIProject Website: Security in autonomous vehicular transportation
News coverage: The Epoch Times,Driverless transportation, The Atlantic, 163 Tech News (网易科技新闻), 爬车网
7. Security of Unmanned Aerial Systems (UAS)

Unmanned Aerial Systems (UAS) offer significant potential but also pose serious security and privacy risks. As UAS proliferation continues, regulatory agencies struggle to integrate them safely into airspace and enforce regulations. This project aims to develop automated systems to detect and neutralize UAS that violate controlled airspace. For example, we propose techniques to detect and localize passive drones that do not actively emit signals, by exploiting existing cellular network infrastructure. We will develop both offensive and defensive strategies, leveraging expertise in UAS flight control, CPS security, wireless communications, reinforcement learning and intelligent control. Our goal is to safeguard airspace and ensure the safe operation of UAS.
Funding support: National Science Foundation, SaTC: CORE: Medium: Collaborative: Enforcement of Geofencing Policies for Commercial Unmanned Aircraft Systems, 09/01/2018 - 08/31/2021, PI.8. Cyber-Resilience for Power Systems

This project aims to secure the integration of Distributed Energy Resources (DER) and power aggregators in the electric grid. We propose a Blockchain-based overlay network combined with a Model-Assisted Machine Learning (MAML) framework. This approach enables: 1) Enhanced Security: Mitigates risks in current network and C2 protocols. 2) Proactive Defense: Detects and responds to attacks targeting DER and distribution systems, in a privacy-preserving manner. 3) Grid Resilience: Automates DER enrollment in grid services like demand response and frequency control. 4) Legacy Device Protection: Develops a plug-and-play security module for legacy DER. By combining blockchain and AI, we aim to create a more secure and resilient electric grid.
Funding support: U.S. Department of Energy (DOE), Achieving Cyber-Resilience for Power Systems using a Learning Model-Assisted Blockchain Framework, 06/01/2021 - 6/30/2023, Co-PI (Lead: Virginia Tech).
Completed Research Projects
- Radio-Frequency Interference for Fault Injection and Sensor Manipulation, Army Research Office, 08/2021 - 01/2025, Co-PI (Lead: Virginia Tech).
- Achieving Cyber-Resilience for Power Systems using a Learning Model-Assisted Blockchain Framework, U.S. Department of Energy (DOE), 06/01/2021 - 6/30/2023, Co-PI (Lead: Virginia Tech).
- DURIP: A Millimeter-Wave Communication System for Wireless Security and Networking Research and Education, $249,934, Army Research Office, 04/21/2021 - 04/20/2022, PI (Co-PI: Loukas Lazos).
- Undergraduate Research Apprentice Program (URAP)/High School Apprentice Program (HSAP) Supplement, $15,000, Army Research Office, 05/15/2021 - 08/15/2021, PI (Co-PI: Loukas Lazos).
- In-band Wireless Trust Establishment Resistant to Advanced Signal Manipulations, Army Research Office, 01/01/2019 - 12/31/2021, PI (Co-PI: Loukas Lazos).
- SaTC: CORE: Medium: Collaborative: Enforcement of Geofencing Policies for Commercial Unmanned Aircraft Systems, National Science Foundation, 09/01/2018 - 08/31/2021, PI.
- SpecEES: Secure and Fair Spectrum Sharing for Heterogeneous Coexistent Systems, National Science Foundation, 10/1/2017-9/30/2020, Co-PI (with PI Loukas Lazos and Co-PI Marwan Krunz) (Project website)
- Toward High Performance Tactical Multi Hop Wireless Networks via Exploiting Antenna Reconfigurability, Office of Naval Research, 6/1/2016-5/31/2019.
- EARS: Collaborative Research: Crowdsourcing-Based Spectrum Etiquette Enforcement in Dynamic Spectrum Access, National Science Foundation, $360,000, 1/1/2015-12/31/2018, PI (Co-PIs: Ryan Gerdes and Bedri Cetiner). (Project website)
- TWC: Medium: Secure and Resilient Vehicular Platooning, National Science Foundation, 8/1/2014-7/31/2019, $1,229,923, Co-PI (PI: Ryan Gerdes) (Project website)
- CAREER: Toward Cooperative Interference Mitigation for Heterogeneous Multi-hop MIMO Wireless Networks, $489,999, National Science Foundation, 7/1/2014-6/31/2019, PI (Project website).
- CSR: Small: Collaborative Research: Towards User Privacy in Outsourced Cloud Data Services, $175,000, National Science Foundation, 10/1/2012-9/31/2015, PI.
- Proving the Possession of Multi-Owner Data in the Cloud, $2,500, Amazon AWS Research Grant, 2014-2016
We thank the generous support of:



